Docker Uses Which Linux Kernel Feature to Provide Data Integrity
Docker Desktop uses the dynamic memory allocation feature in WSL 2 to greatly improve the resource consumption. The second argument is platform linuxamd64.

Best Practices For Docker Security In 2021 Bluetris Technologies
This independence is the intention of containersthe ability to run multiple processes and apps separately from one another to make better use of your infrastructure while retaining the.

. This will allocate and attach the bip to the bio. Accounts for cpu memory IO and other resources used within a container. Cgroups in Linux limits the resource usage CPU memory disk etc of a process.
In our setup each Docker container that is launched and any child processes forked inside the container are contained in a given cgroup. Docker exposes these Linux kernel capabilities either at Docker daemon level or at each Container level. Docker uses several foundational Linux kernel features to provide isolation to your running processes and the files associated with them.
Individual pages containing integrity metadata can subsequently be attached using bio_integrity_add_page. Docker will not stop you from running such an image on an older kernel as it simply does not care whats inside an image nor does it know what kernel was used to. Docker engine uses Linux kernel features like Namespaces and Cgroups to provide basic isolation across Containers.
Compared to a standard Docker deployment our solution enables run-time veri cation of container applications at the cost of a limited overhead. Optionally enforces limits for the use of those resources eg. Feature of the Linux kernel.
The Docker technology uses the Linux kernel and features of the kernel like Cgroups and namespaces to segregate processes so they can run independently. Once ADI is enabled and version tags are set for ranges of address space of a task the processor will compare the tag in pointers to memory in these ranges to the version set by the application previously. It is also possible to leverage the existing system like TOMOYO AppArmor SELinux GRSEC etc.
In fact IMA maintains a TCG-compliant Integrity Measurement Log and it is the. Bio_free will automatically free the bip. A kernel subsystem can enable data integrity protection on a bio by calling bio_integrity_alloc bio.
I am volunteering to set up Docker on Ubuntu 1804 with real-time kernel 41816-rt9 for a robotic application in an academic setting. And data integrity for services running in soft warised environmen ts. It is prefixed with jwe.
On a 49 or lower kernel docker run centos6 bash will work fine. An example of the power of cgroups is to use docker run flags such as memory or cpus to limit resources when running a new container. Cgroup s are a Linux kernel feature that.
The Linux Integrity Measurement Architecture the OpenAttestation platform and the Docker container engine making it practical and readily available in a real-world scenario. We use the Linux IMA technology for creating the measurement list because it does not require any modification to Linux as it is already integrated into the Linux kernel since version 2630 and it is considered by the TCG as a favourable technology for run-time integrity verification. Just as a reminder on how Docker works.
Access to memory is granted only. The Beta program is aimed at early adopters who would like to try Docker Desktop for Linux and provide feedback. Kernel Security and Implementation Docker makes use of several Linux Kernel features to deliver its functionality in a secure manner.
As noted above Docker images that include software which relies on bleeding edge kernel features will not work on kernels that do not have those features which should be no surprise. Every Docker container gets its own Linux Control Group cgroup by default. To provide the required security to Dockers in addition to the inbuilt features of security.
To indicate that the encryption scheme is JSON web encryption scheme. Resources such as CPU memory and IO can be limited using cgroups. More often but not always.
This means Docker Desktop only uses the required amount of CPU and memory resources it needs while enabling. Control groups or cgroups is a Linux feature that allows the limiting of resources for a particular group of processes. The third argument is dockeriolibrarybashlatest which points to the image we want to encrypt.
On a host with kernel 419 eg. One of these features that we make use of is cgroups. Namespaces - Isolation SELinuxAppArmour Data Integrity Seccomp default Privileges.
Ubuntu 1804 try docker run centos6 bash. In addition WSL 2 provides improvements to file system sharing boot time and allows access to some cool new features for Docker Desktop users. Docker Desktop is an easy-to-install application that enables you to build and share containerized applications and microservices.
SPARC M7 processor adds the Application Data Integrity ADI feature. Denying further memory allocation or throttling cpu usage. Youll find it segfaults exit code 139 because that old build of bash does something that greatly displeases the newer kernel.
Docker uses cgroups to enforce resource isolationCgroups are a part of the linux kernel and can be used to restrict the resources available to groups of processes. There are several security features included in modern Linux kernels. This flag tells containerd to only encrypt the linuxamd64 image.
Why is Docker so Popular Other Kernel Security Features. ADI allows a task to set version tags on any subset of its address space. Docker will not run critical real-time tasks in this application but the intention is to deploy partially containerized system on one machine to simplify the setup and testing with different software versions.
Storage drivers used by Docker are Aufs Device Mapper and Btrfs 18. Docker uses the resource isolation features of the Linux kernel such as cgroups and kernel namespaces and a union-capable file system such as OverlayFS to allow containers to run within a single Linux instance avoiding the overhead of. Advanced isolation can be achieved using Linux kernel features like Capabilities Seccomp SELinuxAppArmor.
Docker Desktop for Linux DD4L is the second-most popular feature request in our public roadmap.

8 Monitoring Linux And Windows Using Prometheus And Grafana With Node Exporter And Wmi Exporter Linux Online Training Monitor

Running Sap Nw 7 52 Sp4 Trial In Docker In Windows Subsystem For Linux 2 Sap Linux Disk Image

Keahlian It Yang Dicari Perusahaan Ditahun 2020 Teknologi Informasi Inovasi Profesi

Classical Big Data Reading Cap Theorem Theorems Big Data Data Science
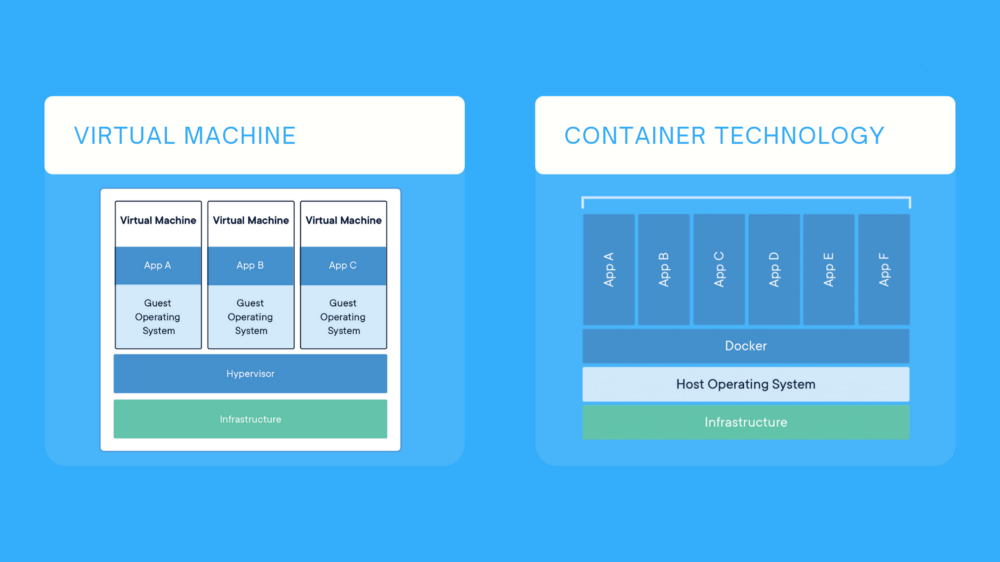
Understanding The Docker Containers Geek Culture

Trusty And Security Services Reference Project Acrn V 2 1 Unstable Documentation

Introduction To The Linux Virtual Filesystem Vfs Part I A High Level Tour Star Lab Software

Seccomp Data Structure In Linux Kernel Download Scientific Diagram
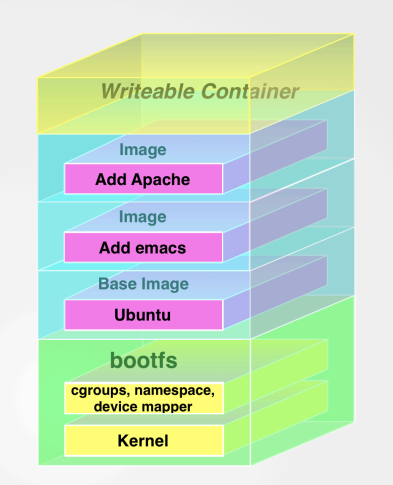
Understanding Docker Container Architecture Collabnix

Architecture Of Linux Kernel I O Stack Download Scientific Diagram

Docker Basics Breakout Hacktricks

Seccomp Data Structure In Linux Kernel Download Scientific Diagram

The Open80211s Stack Integrates Into The Linux Kernel Download Scientific Diagram
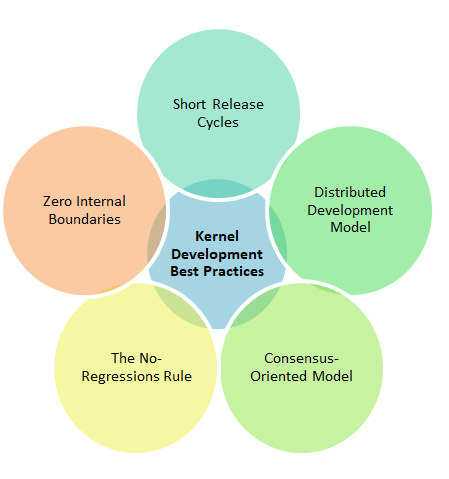
Linux Kernel Development Best Practices By Packt Pub Medium

In This Article We Are Going To Cover Real Time Docker Interview Questions And Answers Interview Questions Interview Questions And Answers Question And Answer
Kernel Privilege Escalation Attack Model Download Scientific Diagram

This Article Provides A Step By Step Guidance On Importing Exporting Oracle Database Dump To From Rds Oracle Using S3 I Pump And Dump Oracle Database Oracle

Learn How To Disable Or Turn Off Lock Screen On Ubuntu 18 04 18 10 Desktop Turn Ons Learning Turn Off
Comments
Post a Comment